 The Importance of Indoor Security
The Importance of Indoor SecurityIntelligent buildings need more than video surveillance to keep people and data safe in today’s landscape. The concerns buildings face have changed drastically in recent years and so to have the tools that protect them. From physical intrusion and property theft to data exfiltration and eavesdropping, it’s never been more important to bridge the gap between physical and digital security to keep buildings, and everything within them, safe.
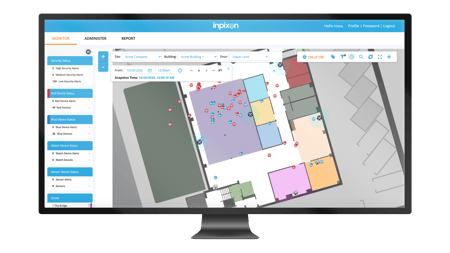
Secure any site with precise indoor positioning and wide spectrum RF detection. Leverage Inpixon to cultivate situational awareness within your buildings by detecting wireless devices and their movements. Our indoor security solution, Inpixon Aware®*, gives you both visibility into your facilities and a robust wireless intrusion detection solution in a single, live security dashboard, so you can make key decisions around security, risk mitigation and public safety, at scale.
AWARD WINNER
2022 Cyber Security Global Excellence Gold Award

The Globee Awards for Cyber Security Excellence honors industry leaders in security and information technology. Inpixon Aware was recognized as a Gold Winner for Security Product and Service for Government.
Learn MoreAWARD WINNER
Security Excellence - IoT Evolution

"Security is clearly the greatest concern for companies deploying IoT solutions. These winners commitment to securing devices and networks sets them apart. We are certain these innovators will continue to lead the market into the next decade and beyond."
Rich Tehrani, CEO | TCM
Enterprise Class, Government Grade
Trusted by high security and federal government agencies to help comply with directives and secure areas with top secret and classified conversations, materials, and activities.
End-to-End Mobile Device Security
Leverage an award-winning technology that gives you a comprehensive set of tools to meet your indoor security needs. Enhance security, mitigate risk and make informed decisions.
Scalable Solutions
Support multiple location data use cases to meet diverse organizational needs. Our modular architecture provides versatility and investment protection to meet your evolving needs.
Inpixon Aware®, our wireless device detection and positioning solution, gives you the digital situational awareness needed to make key decisions around security, risk mitigation and public safety. Create secured indoor spaces with Inpixon Aware.